Managed Security Services
Powered by:
Enterprise-grade cybersecurity delivered on-demand
equals peace-of-mind
Regardless of your size or industry, organizations like yours face common barriers to cybersecurity effectiveness. DC Consulting levels the playing field with access to powerful cybersecurity.
Modern organizations like yours need protection delivered in a way that is simple, accessible, and fits your budget. In the face of today’s cybersecurity challenges, it makes sense to partner with a firm like DC Consulting.
By partnering with SilverSky, DC Consulting provides one of the most comprehensive sets of cybersecurity services in the industry. Delivered as a managed services model with on-demand access, our services are backed by enterprise-grade, integrated technology and the skilled expertise to run it. The security operations centers monitors your on-premise, cloud, or hybrid environment for threats 24x7x365 — with real-time remediation capabilities.
Highlighted Services That Strengthen Your Security Posture
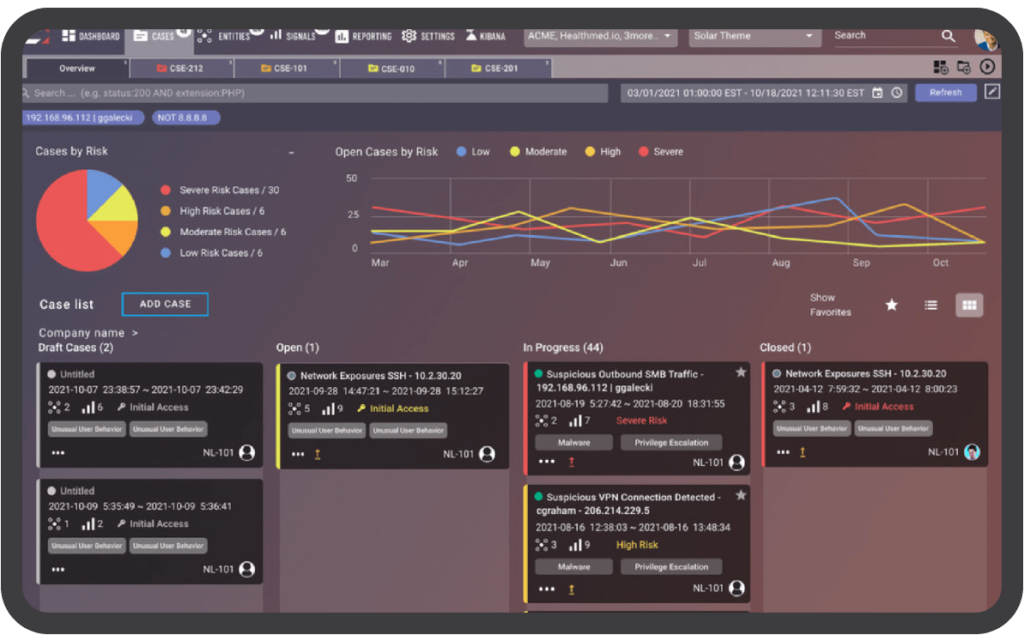
ADAPTIVE ANALYTIC DETECTION (AAD)
Reduce Noisy Alerts 97% More Effectively Than Typical SIEM
DC Consulting’s managed security services leverage machine learning and AI-based behavioral analytic detections to analyze massive log and alert volumes to detect behaviors that elude rules and signatures. As a result, AAD recognizes patterns and threats and gives you a handful of curated cases instead of thousands of alerts. This gives you an extraordinarily high noise-to-signal ratio, eliminating alert fatigue and improving your security posture with a more accurate, focused view of your risk profile.
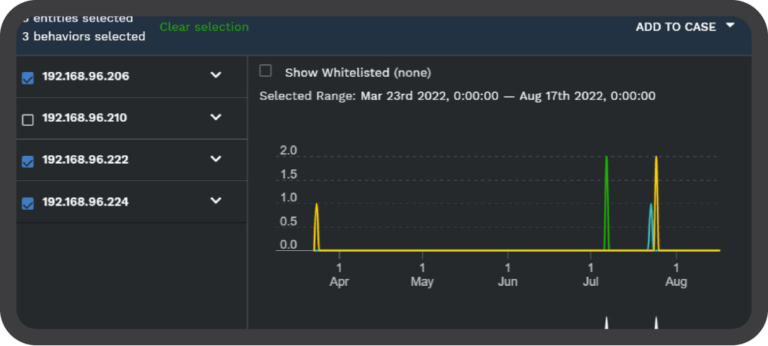
Adaptive Analytic Detection (AAD) at a Glance

Persistent Behavior Tracing (PBT)
Find Threats Others Miss, Fill Gaps in Your Security Posture
DC Consulting Managed Security Services, powered SilverSky, has a unique method of storing de-duplicated behavior attributes associated with each event on a per entity basis. This allows for a historical contextual view over an unlimited time frame without massive storage requirements. We call it Persistent Behavior Tracing (PBT).
PBT utilizes a unique hash sum, calculated at processing time, from fields describing each behavior. PBT identifies behaviors via a variety of detection methods determined by the analytics that generate that behavior, and each occurrence of a behavior is then tracked using a set of fields specific to that behavior. The result is a system that tracks attack vectors in real-time, saves relations indefinitely, and identifies associations based on the threat behavior.